Data security and compliance
Security is an essential element in ensuring the confidence of platform users.
Data security
Data encryption
Data encryption at rest and in transit depends on the storage service providers for S3 and the database.
In the Kubernetes deployment, the Helm Chart Qalita does not contain a configuration for default encryption. It is up to the user to configure the encryption of data at rest and in transit.
Storage:
Queries:
Query encryption depends on the configuration of network endpoints and certificates used. It is the user's responsibility to configure network endpoints and the provision of valid and exclusive certificates to guarantee security.
When deployed on Kubernetes, the default the Helm Chart Qalita requires cert-manager to be properly configured to provide valid and exclusive certificates for network endpoints.
The following endpoints are created:
backend (api) frontend (webapp) doc (documentation)
Access management
Access to the platform is managed by an authentication and authorization system.
Log management
There are two types of logs:
-
User activity logs User action logs are stored in the platform's relational database in the
logstable. They are used to audit user behavior, both on the webapp and with agents, thanks to the mutualization of authentication tokens provided by the backend for both the webapp and agents.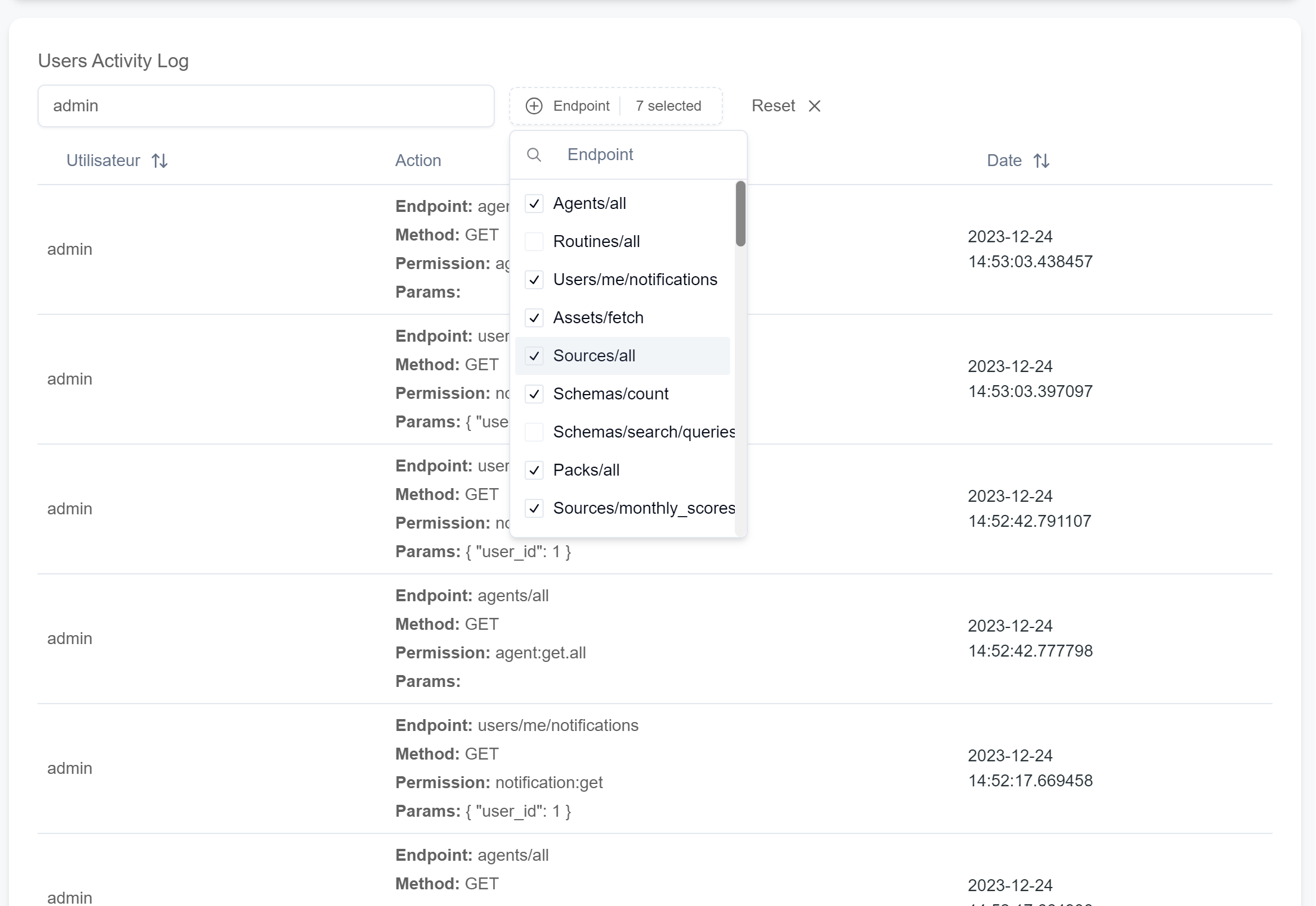
-
Task execution logs Task execution logs are stored in the platform's S3 storage. They are used to audit pack behavior on data. You can consult them in the "LOGS" drawer on the platform's Agent page, or directly in S3 storage in the
logsbucket.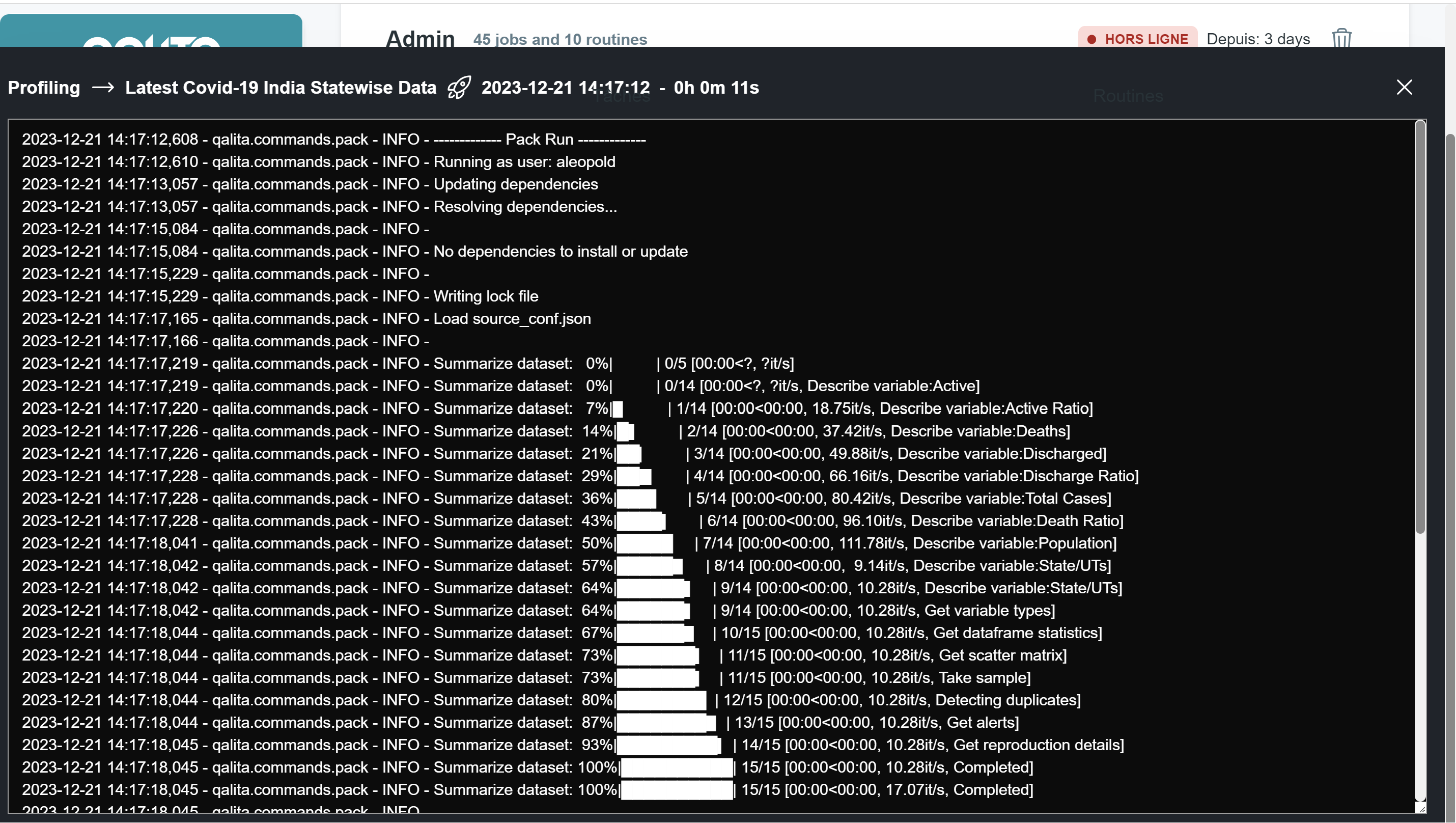
Metrics management
Metrics are calculated by the packs and stored in the platform's relational database. They are used to generate analysis reports, dashboards and tickets.
Some packs generate metrics that are directly linked to data without any aggregation operation. These metrics are stored in the platform's relational database. They are sensitive and must be accessed with the same level of security as the source data.
Be sure to read the package documentation to understand the metrics generated and their sensitivity.
Data compliance
Depending on your industry, you may be subject to data compliance regulations and standards.
The platform aims to follow and comply with the following regulations and standards without guaranteeing results or certification: